A quick review of my CRTL journey
After completing Sektor7’s Malware Development/Evasion track last year, I’ve decided to start 2023 with the long-awaited Red Team Ops 2 (RTO2) from Zero-Point Security, which is a prerequisite course for obtaining the Certified Red Team Lead (CRTL) certification.
Being already aware of the quality of Zero-Point Security courses after completing the RTO1 and the awesome “C2 Development in C#”, I was looking forward to seeing what rastamouse had to offer on RTO2… 👀
The Course
As described on Zero-Point Security’s own website, RTO2 should be understood as a continuation of RTO1, not a replacement. This right off the bat means that you are expected to know the core concepts covered in RTO1, which is an extensive course (really!) and teaches you a lot about Red Team operations.
If you’re new to RTO1, I strongly recommend you give it a go, even if you’re an experienced Red Team operator. As usual in Zero-Point Security courses, the material always stays with you after purchase and is constantly updated by rasta, which turns out to be a great reference for Red Team/Pentesting concepts. I particularly bought the first version of RTO1 back in 2020 and since then, a lot of new stuff has been added. I would say it has almost doubled its content compared to the 2020 version.
Speaking of RTO2, the course focuses on evasion and more advanced OPSEC tactics. It will teach you how to build a resilient Red Team infrastructure, concepts about session prepping with OPSEC considerations, how to build a custom C2 profile and some basis to write C#/C++ tools that will serve to evade EDR protections. Two Microsoft 365 Defender protection features will be covered in more detail (ASR and WDAC) and to be honest, I didn’t know about them until I took the course.
Unlike most of the Red Team/Pentesting labs out there, the RTO2 lab focuses much more on “research” than on a “goal to be achieved” (which usually means escalating privileges from limited access, move laterally and compromise domains/forests). It took me a while to understand this and forget the idea that I was there with the aim of achieving high privileges and you know… collecting something like “flags” along the way. That’s NOT the purpose of RTO2 lab and you are already supposed to have administrative privileges to all lab machines (including the CA and DC). Therefore, the lab machines will be used exclusively to validate the tactics and techniques learned throughout the course and that’s it. One of the lab machines (called “Windows Attacker Machine”) will contain Visual Studio so you can write and debug your tools. This same machine also has a folder containing some tools (C:\Tools) that can be used during the lab, since the Guacamole environment provided (which runs in the browser) does not have internet access to download tools and you can already imagine the pain of copying tools from your host to a browser GUI session.
Regarding the content, course modules are all very well structured, in a simple and direct language that I like a lot. At the same time, the content leaves some minor “gaps to be filled” in order to solve the lab exercises and this is clearly done on purpose by rastamouse. Unlike RTO1 that goes hand in hand and gives everything ready to run, RTO2 expects you to go beyond the material and do your own research work.
The course costs 400 pounds (roughly $540 CAD) and provides 40 hours lab access + 1 exam voucher + access to the Discord RTO2 students channel. Each lab extension costs 15 pounds and gives you more 40 hours. Honestly, I think the value is fair for the quality and mainly for the important fact that you will continue to have access to the material and its updates in the future.
Exam
Students are expected to collect 4/4 flags that will be spread between servers and workstations within 72 hours over 5 days - you can stop the exam and resume it whenever you want, as long as it is within the 5 days duration from the date you started.
Particularly, I found the exam straight to the point. If you solved all the lab exercises, having replicated everything that was taught and saved your malleable C2 profile and all the C#/C++ codes you’ve written to evade defenses throughout the lab (especially to circumvent ASR/WDAC), you shouldn’t have much trouble clearing the exam in the 72 hours. I completed the exam in ~9 hours, starting at 7 PM EST (7 Jan, 2023) and ending at 4:04 AM EST (8 Jan, 2023), having gotten the first flag at 9:52 PM:
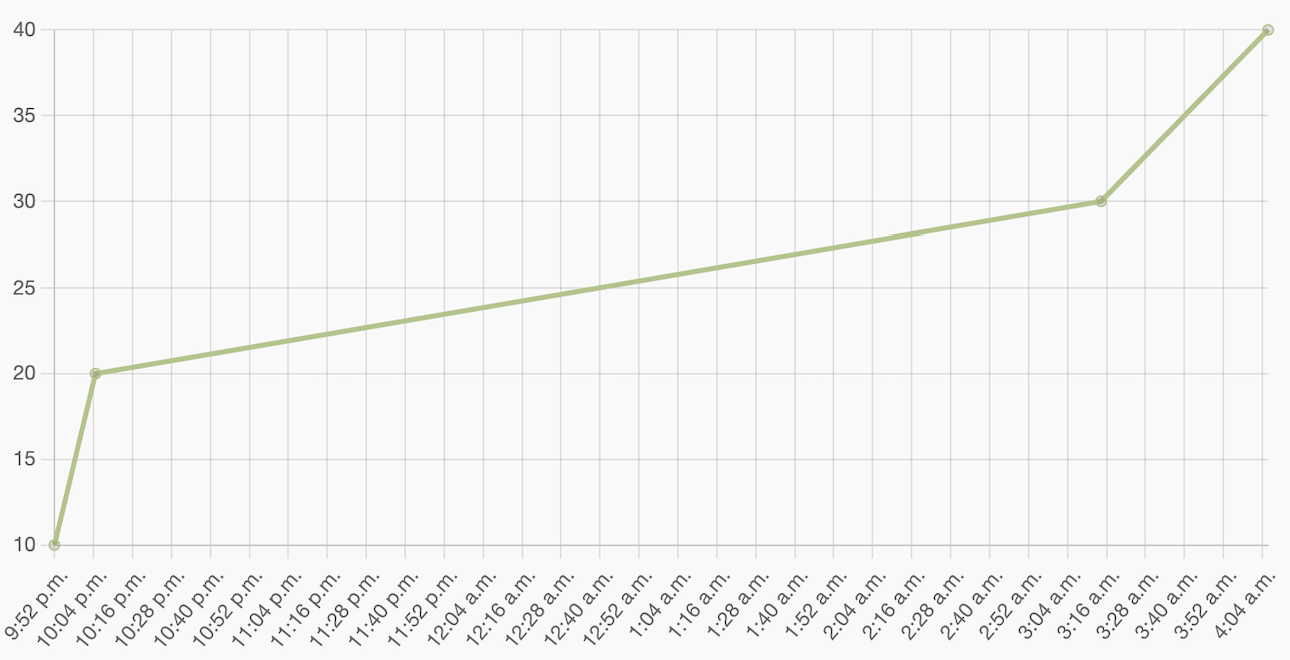
It is important to highlight that the exam combines concepts from the RTO1 with the RTO2, so keep in mind that it may cover subjects that were NOT taught during the course but are discussed in detail in the RTO1 (and that’s why once again I recommend you to do RTO1 ;).
At the end of the day, I think the exam does a good job of validating what you learned in the course. It might not be that easy as it requires you to think outside the box in some situations (I mean, a little more enumeration and you’re good), but it also shouldn’t put you in crazy rabbit hole scenarios or anything nonrealistic that breaks your balls. It’s pretty fair.
After the 5 days of the exam (plus +1 hour), I received my result by email:
Conclusion
It is definitely a worthwhile course. In fact, the Zero-Point Security courses have been the best I have taken in terms of value for money. The material stays with you and is updated from time to time. The lab is also there, you can return whenever you want paying a fair maintenance fee.
So if you’re looking for a course that focuses on EDR evasion combined with Red Team aspects (including OpSec considerations, so little covered by most Red Team courses out there), give RTO2 a try.
Last but not least: RTO3 when??? xD