Bypassing “RemoteSigned” execution policy in PowerShell
In a recent assumed breach assessment I came across an environment that enforced the PowerShell “RemoteSigned” execution policy via Group Policy. “RemoteSigned” execution policy requires that all scripts and configuration files downloaded from the Internet are digitally signed by a trusted publisher.
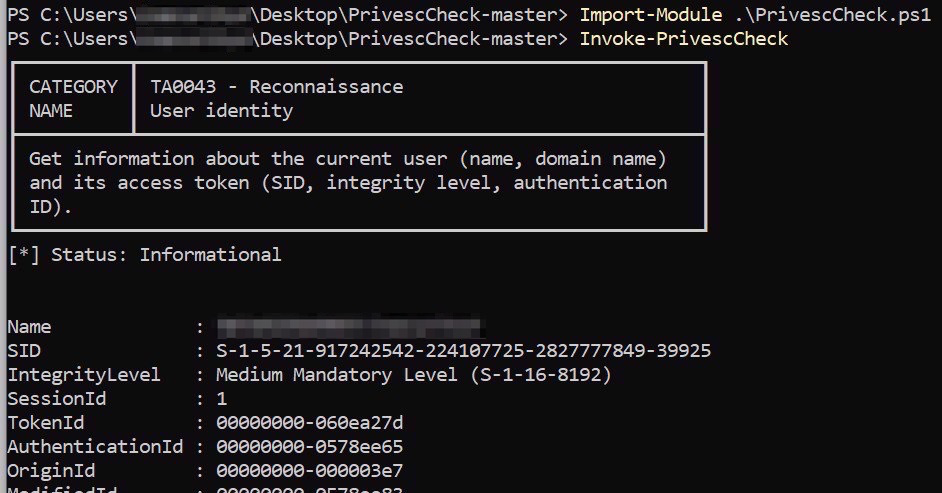
When trying to load any PowerShell script downloaded from the Internet (like the awesome PrivescCheck from itm4n), the following error message was returned:
The file <file> is not digitally signed. You cannot run this script on the current system. For more information….
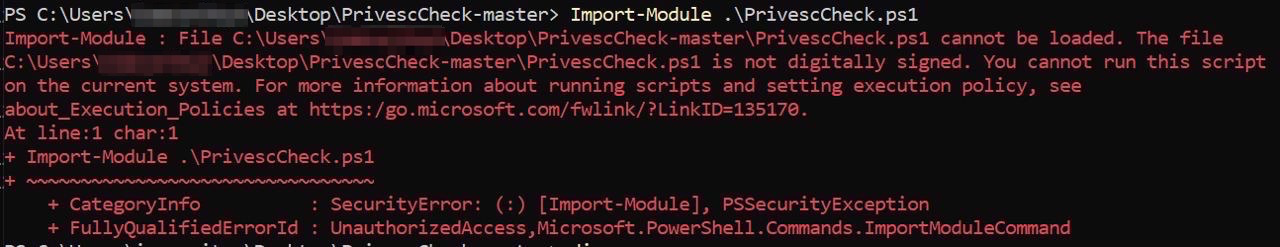
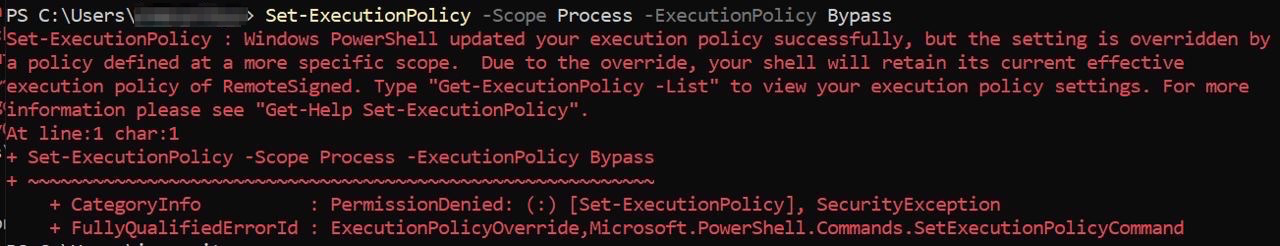
Even if I tried to manually set the execution policy to “bypass”, it would be overridden as the “RemoteSigned” was defined in a more specific scope (i.e. “MachinePolicy” scope and set by Group Policy):
Reading more about this policy in Microsoft’s documentation, it seems clear that the restriction applies to scripts that come from the Internet:

But how does it know that my script came from the Internet…?

The answer should probably be… Mark-of-the-Web!
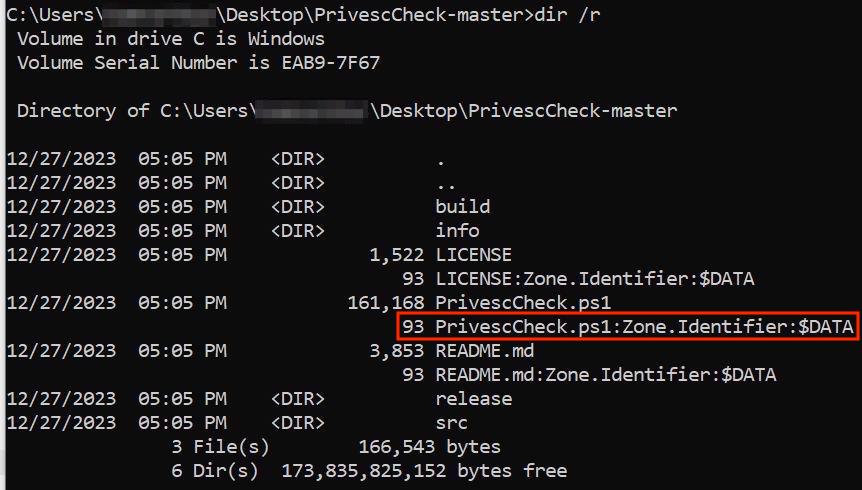
Windows uses Mark-of-the-Web (MotW) to indicate that a file originated from the Internet by appending a Zone.Identifier Alternate Data Stream (ADS) to the downloaded file (dir /r command will bring us the existing ADS file attributes in the directory):
By opening the “PrivescCheck.ps1:Zone.Identifier:$DATA” file with notepad.exe, it contains the “ZoneId = 3”:
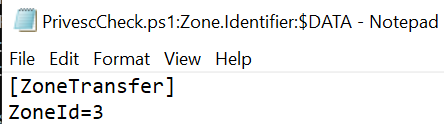
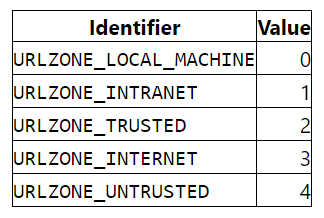
As you may already expect, this Zone ID is associated with the “Internet” (from Microsoft Docs):
If MotW really is the villain here, all we need to do is clean it up:
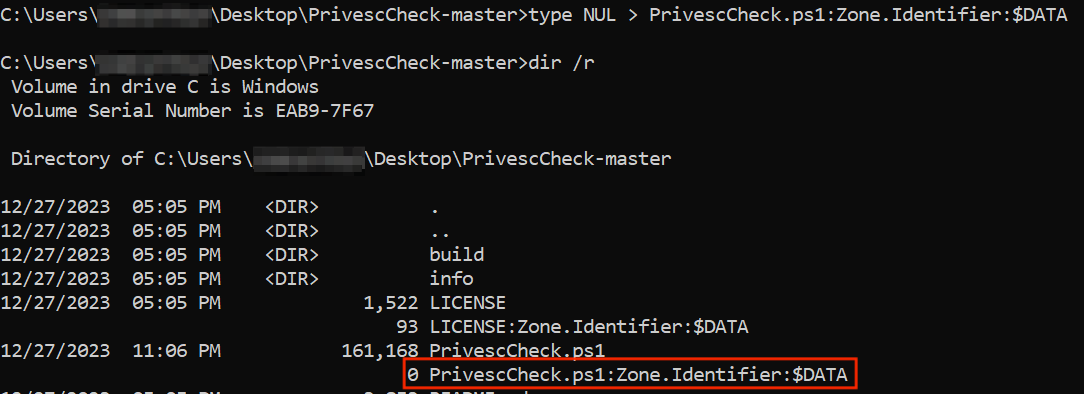
… and voila!
The PowerShell script was loaded under the enforced “RemoteSigned” execution policy without even being digitally signed! 🙂