Certified Red Team Expert (CRTE) - Review
I recently took the amazing “Windows Red Team Lab” course from PentesterAcademy, a prerequisite course for the Certified Red Team Expert (CRTE) certification. I must confess that I had my eye on this course for some time, mainly due to the topics covered in its content (anyone who knows me knows how much I like Active Directory exploitation and everything it involves ;). As I was a little tired of the HackTheBox boxes routine, I decided it would be a good time to start the lab and learn new AD stuff.
The purpose of this review is just to pass on a little of the experience I had in the lab and in the exam. Obviously, I have no intention of providing spoilers, lab walkthrough nor anything like that.
The Lab
First of all, it should be noted that Windows RedTeam Lab is not an introductory course. Indeed, it is considered the “next step” to the “Attacking and Defending Active Directory Lab” course, which is a prerequisite course for obtaining the Certified Red Team Professional (CRTP) certification. Thus, if you are not familiar with Active Directory exploitation, I highly recommend that you take the “Attacking and Defending Active Directory Lab” course first before proceeding with Windows Red Team Lab.
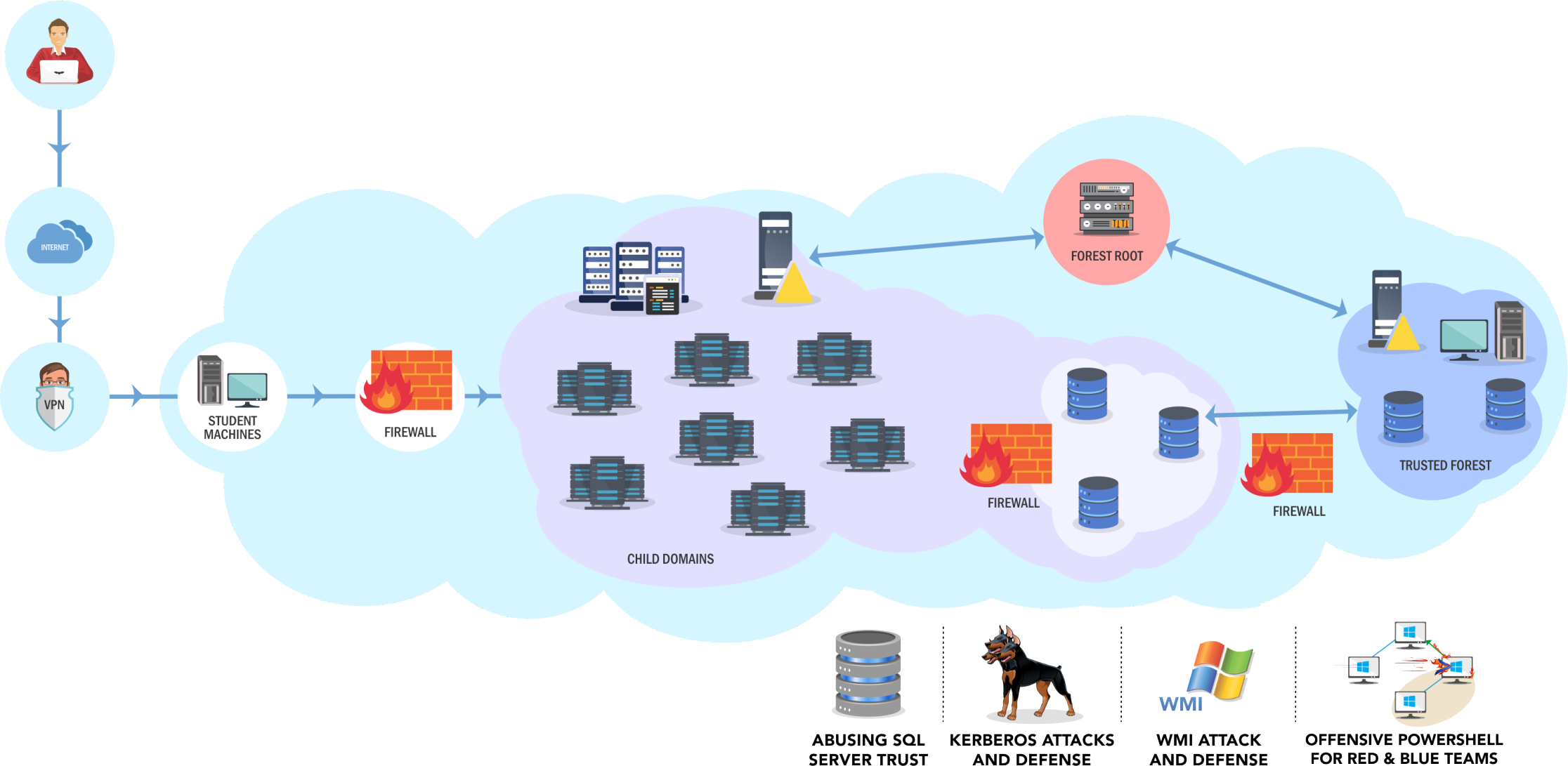
That said, the image below reflects exactly what will be found during the lab:
Pentesteracademy offers three purchase options for the course:
- 30 days lab access
- 60 days lab access
- 90 days lab access
Since I hadn’t taken the “Attacking and Defending AD Lab” course before, I was worried that I couldn’t manage the lab in 30 days. So… I decided to buy 60 days of access, in the hope that it would be enough time to compromise all the boxes and collect all the flags.
The lab starts with a non-privileged RDP access on a host positioned in the student network. All hosts in the environment (including the initial one) are fully patched and contain the latest Windows operating systems, plus UAC enabled, Windows Defender, AMSI, Constrained Language Mode and so on. No specific exploits are needed in the lab, it’s all about AD misconfigurations.
The student will be able to choose one of the two “difficulty modes” available in the lab: “High” and “Normal”. In case of “High” difficulty, you will only be able to connect to your initial box (student machine) via RDP. In other words, you probably shouldn’t be able to use the student machine as a “tunnel” or “pivot point” to the lab network, which would allow to execute commands from your host (from my linux, for example). By default, the difficulty in the lab is set to “High”, but every month a student can change it up to two times if he wants. I decided to keep the difficulty at High to make things more challenging and also force myself to perform all the exploitation from a Windows box (as a pentester I almost always work from a Linux box in my day-to-day and I really wanted to get out of my comfort zone).
To be honest, I find the lab quite challenging. Mainly because it requires that you already have some background on topics like Constrained and Unconstrained Delegation, Kerberos attacks (Kerberoast, ASPREProast, Golden/Silver Tickets, etc), SQL Server Trusts, Intra-Forest and Inter-Forest Trusts and enumeration… a lot of enumeration. I can say that I was stuck for several moments precisely because I still did not understand some of these concepts. Either I had some knowledge gap to be filled (which was what happened in most cases) or I hadn’t enumerated it well enough.
The 3.5 hours of course material videos will definitely not cover all the content covered by the lab and you will still need to conduct research on your own. Here are some references that were essential for me during the course:
- Wagging the Dog: Abusing Resource-Based Constrained Delegation to Attack Active Directory (Must-read!)
- Hacking SQL Server Stored Procedures – Part 2: User Impersonation
- SQL Server – Link… Link… Link… and Shell: How to Hack Database Links in SQL Server!
- S4U2Pwnage
- A Guide to Attacking Domain Trusts
- It’s All About Trust – Forging Kerberos Trust Tickets to Spoof Access across Active Directory Trusts
- Roasting AS-REPs
And some of the main tools I used in the labs:
- Mimikatz
- PowerUp, PowerUpSQL
- Rubeus, Kekeo
- Powerview, AD-Module, BloodHound
- Nishang, Powercat
- PowerSploit, Inveigh
If you have been stuck in the lab for days without being able to proceed and running out of ideas, I strongly recommend contacting the support team. Seriously, the guys are fantastic and have an incredible response time. Obviously, they will not provide you with any spoilers, but they will most likely point you to some directions and give you some hints on the path you should take. Any other type of problem, such as a host or service that has stopped responding, do not hesitate to contact them … usually the problem is solved within few hours (or even minutes).
Even before the 60 days, I was able to compromise all the hosts in the lab and collect all the flags /o/. I scheduled my exam immediately after clearing the lab.
The Exam
Students will have 48 hours to complete the hands-on certification exam, aiming to compromise all 8 servers available in the exam lab. As in the lab, the servers will be spread among forests and will have different configurations. PentesterAcademy claims that if you are unable to compromise all 8 servers, you will still have the chance to pass if you submit a good quality report (for example, a report suggesting practical mitigations and open source tools, citing talks and blog posts, a detailed narrative, etc). Even so, a minimum of 3 compromised machines is required to give you any chance of passing.
I didn’t find the exam so difficult, since it is well-aligned with the contents of the lab. I don’t intend to give spoilers here, but out of all 8 machines, only one machine made me repeat the enumeration scripts a few times to find a way. It doesn’t even compare to the many times I’ve been stuck in the lab, running out of ideas for days :’(. If you have completed the lab, the 48 hours are likely to be more than enough to compromise all the machines, having enough time to create a good report (IMHO).
A few hours after submitting the report, I received an email confirming my approval: